Long story short, during 2006 a series of mysterious posts on Craigslist gave phone numbers which led to number station-like recordings, which were ultimately revealed to be a project by a group of hackers to test the ability of the general cryptography community. The messages and decoding methods used were revealed in a Def Con panel... except for one message, which purportedly contained sexual implications of a famous personality that could be litigation-worthy.
Well shit, I can't NOT try and get into that. Let's crack it!
Unfortunately all of the discussion on the topic seems to have been lost to time, and even if we did have it it sounds like not much progress was made anyway.
But we do have one thing they didn't have: the method! Unlike those trying to solve these before the reveal, we at least know how the messages were enccoded. That plus we have some idea of the format of both the key and the text. So working with that...
First thing we might consider is that computers see everything as a series of ones and zeroes. The way the ASCII table is set up, the ones and zeroes of a certain character tell you something about that character... values below 31 (000xxxxx) are unprintable special characters and won't be used. Values from 32 to 63 (001xxxxx) are punctuation and numerals. The next two sections are mostly letters, with some punctuation to fill each set out to 32; 010xxxxx are uppercase and 011xxxxx are lowercase.
Combine that with xor, which basically tells you which bits of a sequence "agree" or "disagree" with the corresponding bits of the other sequence. Thus, the upper three bits of each number in the encoded sequence tell you whether the section one character is from "agrees" with the section the other character is from. Most values are below 32, meaning the characters are from the same section, likely mostly lowercase letters. No values are over 96, which would be punctuation xored with an uppercase letter.
so of course the next thing i did was generate a table of every character xored by every other character

I don't know what I was expecting! (this is exactly what I was expecting)
My next tack was to attempt to line up the username and password pair that ended the other three of the first four messages. There are a couple different formats given ("u:" versus just "u"), but the difference is minimal, so surely something can be found... Yes, sitting there trying to line up the words "dogballs" and "catsex" against a message supposedly containing some lurid sexual content. Good times. Anyway, I didn't find anything, and we'll see why in a moment.
Eventually I remembered that Python has its own in-build xor operator (I made my own...) and combined that with the chr and ord functions to make a much simpler decoder, and used that to make a cribdragger. "dogballs" and "catsex" still didn't turn up any results, so I tried something else featured in multiple of the messages, like the URLs, and "tinyurl" turned up... an interesting result.
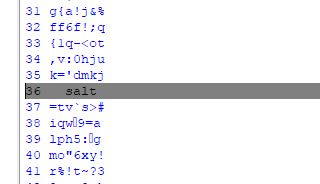
Why yes I am feeling a little bit salty, thank you. The odd presentation of this- the extra spaces preceeding it mainly- at first made me think this was just junk text that happened to form into a word, but nevertheless, I extended the crib phrase to the whole tinyurl and HOLY SHIT
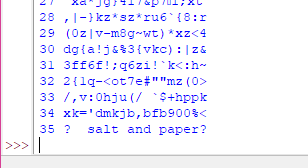
Well, that's a success! The encrypted text was simply missing the username and password text the other messages had. This is probably due to the message being put up by one member without consulting the others, so it ended up with incorrect/incomplete formatting.
Only problem is, there's nowhere to continue from here. Both pieces of text are basically a whole "phrase", with nothing like a partial word or sentence to try completing to continue it...
Since both OTP and message are phrases, we have two lines of attack, guessing the contents of either of them. The OTP seems to be a pun relating to food and paper; given it ends in and is proceeded by a question mark, I don't think it's a punchline, but something like a collection of punny phrases. The message itself, which is likely the part containing "sexual proclivities", is completely opaque due to only having the tinyurl part cleared. The way the encoding works, words from either can be identified by the cribdragger, so I can just sit here throwing in words that might be found in either of them and seeing if anything sensible pops up, but progress is slow. So for now, here I sit with a python script open, throwing all the funny sex words I can think of at it.